CaptivePortalLogin: Captive Portal Login
Hello once again, I am here with a new topic. This subject is somewhat underestimated. So I am here to throw some light and explain its importance. The title is captiveportallogin or “Captive Portal Login“. Now, I need you to understand something about this. Reading the title itself will give an idea. A portal login, that’s it. For now, let us consider that it is a small login system that is available when we are surfing the web.
Let us see an example: A man is going to a bank to open an account. He does an inquiry at the account section. The person sitting there gives him full details about the bank policy. He also explains to him the process for creating an account in the bank. Next, he gives that man a form. It is all about inputting the personal details that a bank holds when a person creates an account. The form is a link that connects an entity to the main database.
Here the bank is a database and the person is an entity. The person fills in all the details, attaches necessary documents, and then submits them. After some days he receives a message that his account has been created. Now the instruction between the entity and database is started. This whole process was possible because of the link provided. The link is nothing but a portal. Do not get confused about the meaning of the word as the bridge between two universes: in the computing world, the synonym is different. Now let us dive deep into it to know the real meaning.
What is a portal?
To know more about what is a portal we need to know about its origin.
History of the internet:
The basic definition says: “Internet is a connection of INTERCONNECTED computer networks“. It came to be in existence in the late 1950s namely ARPANET. Advanced Research Projects Agency (ARPA) received contracts from the defense agencies of the United States of America. New elements were added in the late 1970s like computer networks, Wide Area Network (WAN), packet switching, etc. Computer Science made progress under the mathematical domain.
In the younger stage, it was a project work given to university students. Many other versions also got developed under the same agenda. The most famous NSFNET project established a temporary connection between some Universities. National Science Foundation (NSF) funded and supported this project. From 1989 to 1990 a computer scientist Tim Berners-lee developed the World Wide Web in Switzerland which made fame in the world as WWW.
Working of World Wide Web:
Analyzing the hypertext documents for information transfer and display through a closed network was its main task. Furthermore, the foundation of the below streams changed the whole game. Changes in every commercial activity like long-distance communication, economy, and commerce made a huge impact on daily life:
- Electronic mail system
- Sending messages
- Voice over Internet Protocol service (VoIP)
- Video calling
- Wireless Fidelity (Wi-Fi)
- Social Media
What are Internet Protocol and IP address?
Daily huge amount of data is created and destroyed. The process of sending and retrieval is very complex to understand. An example will help you in this:
Let’s say that you go to the sweets shop and request the shopkeeper to give you some sweets. The shopkeeper weighs them and puts them into a packet or a cart-sheet box. You carry home those sweets in that box.
Understand it by comparison:
- The shop is the source
- You request the shopkeeper
- The sweets are the data generated in the shop
- The box is a packet in which the sweets or data is enclosed
- You are the receiver
- You go home unpack the sweets or data and eat or access it after reaching the address or home
Now, look carefully at the highlighted words. When we combine all the statements, working of Internet Protocol comes into the picture:
The user sends a request to the host or the data source. The source verifies the user information and if entered credentials are valid then the server sends data to the respective user.
Networking works on sending and retrieval of data from source to destination. The info generated from sources travels through generated signals trying to reach towards destination.
This flowchart below will make things super easy
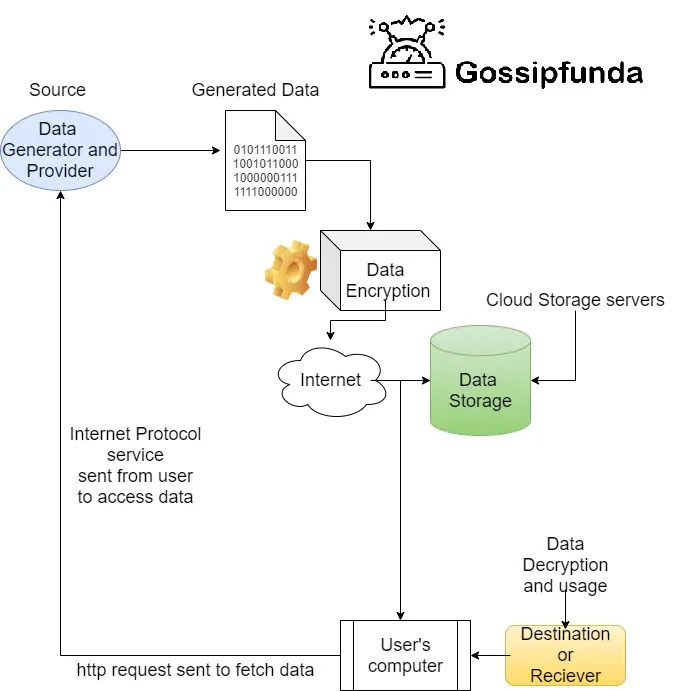
IP address:
Every device has an IP address that is tracked by the website when the device visits the respective website. This IP stores the device location and other info in the form of numbers separated by dots: ‘192.0.0.7’. the location shown is the area or place from where the user accessed the webpage.
User Data Security:
In this whole process, user verification is most important. Keeping this in mind the concept of data encryption was designed. This is where the Captive Portal Login works. It is the idea of modern internet websites. For a particular website we visit for our work, a landing page pops up. As soon as it comes in front of us the page shows login details, sign in option and create an account. Creating this makes you a user of this website. When logged in the webpage shows the full data we need to access. But before login, only an abstract is shown.
Now, all this is monitored by Captive Portal Login.
read also: com.sec.android.daemonapp
What is CaptivePortalLogin?
Captive: Held under control, kept within bounds.
Portal: Path through which activity is happening or going on.
Login: To enter in the site portal.
captiveportallogin: A networking activity that is happening under control.
It is somewhat different from other websites. When you are at a railway station, it provides open Wi-Fi to all for an hour. This makes it vulnerable to hacking. So it asks for a safe login through your email or phone number. It then sends a Time Password (OTP) to you for info verification through a message. When you enter that code, the connection is made available with the router.
HTTP redirected service:
HyperText Transfer Protocol (HTTP): is a TCP service provided by the World Wide Web. The channel sends messages that have predefined encoded numbers.
This is the list of some codes:
- 200: no content
- 302: page not found error, redirect to another page
- 402: page not existing error
- 200: this is only visible to the vendor, it states that the connection is stable
App details and requirements for captiveportallogin:
Package name: com. android.captive portal login
OS: Android
Phone brand supported: made for every android
Note: Browser is needed to run
Advantages of captiveportallogin:
- Comes pre-installed on the phones
- Provides user data security
- Creates a stable bridge for the user to interact with web
- Very helpful in accessing public networks
Disadvantages of captiveportallogin:
- Misbehaves if a system is not stable (developer mode)
- Creates pop-ups like Wi-Fi not found
- Gives connection errors when the HSTS request is changed from the previous one.
- Stops working after some intervals of use
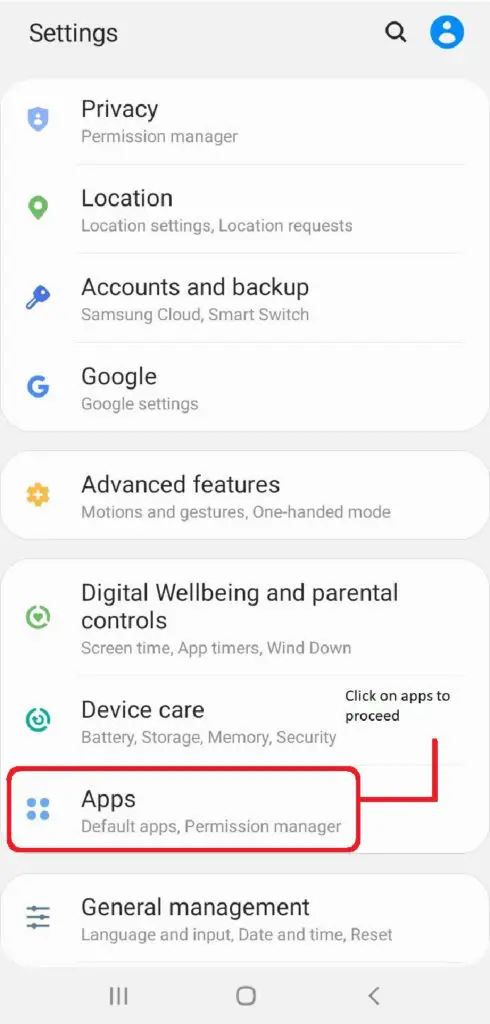
Locating captiveportallogin inside your device:
- Go to the settings app
- Then go to the apps section
- Then go to system apps
- Search for Captive Portal Login
Locating and force stopping inside Samsung Galaxy:
- Go to the settings app
- Then go to Applications
- That is the top right corner, click on three dots
- Show system apps
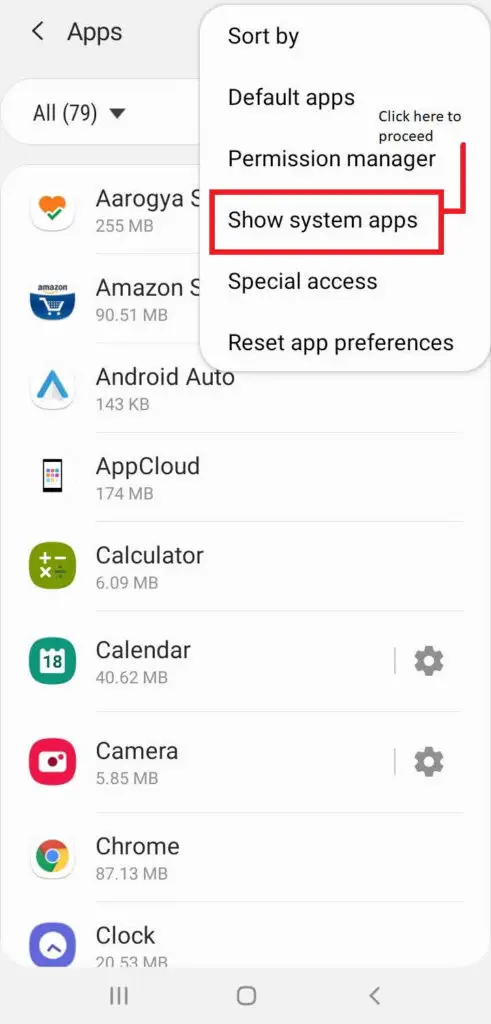
- In the search bar start typing Captive Portal Login
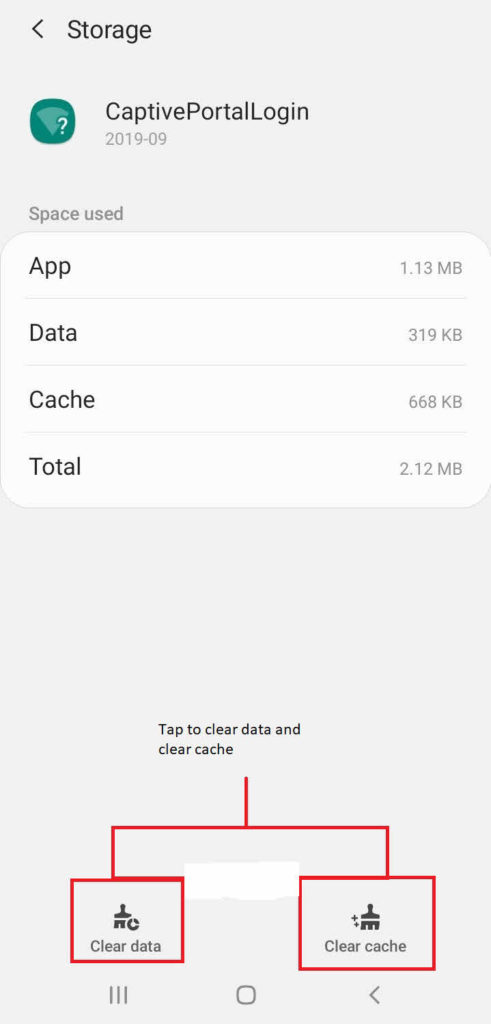
To clear data and clear cache:
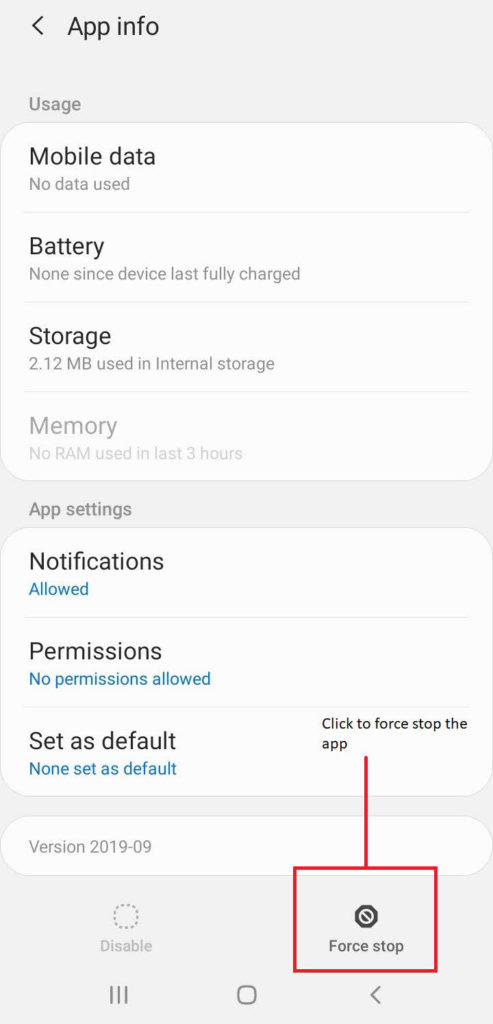
To Force Stop CaptivePortalLogin
Locating and force stopping inside Vivo smartphones:
- Go to settings
- Search for more settings
- Tap on the Applications option
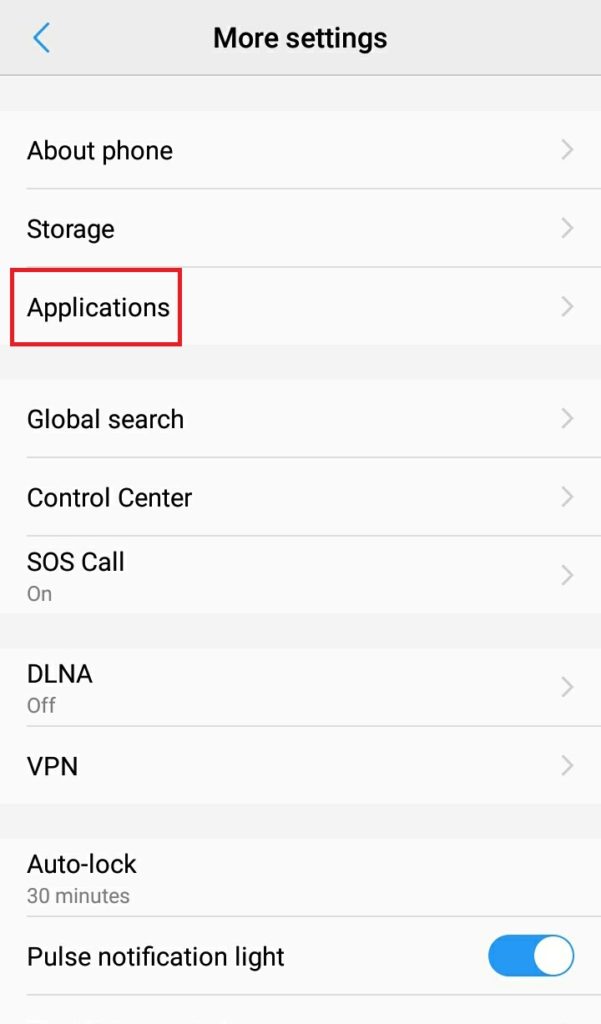
- Tap on all
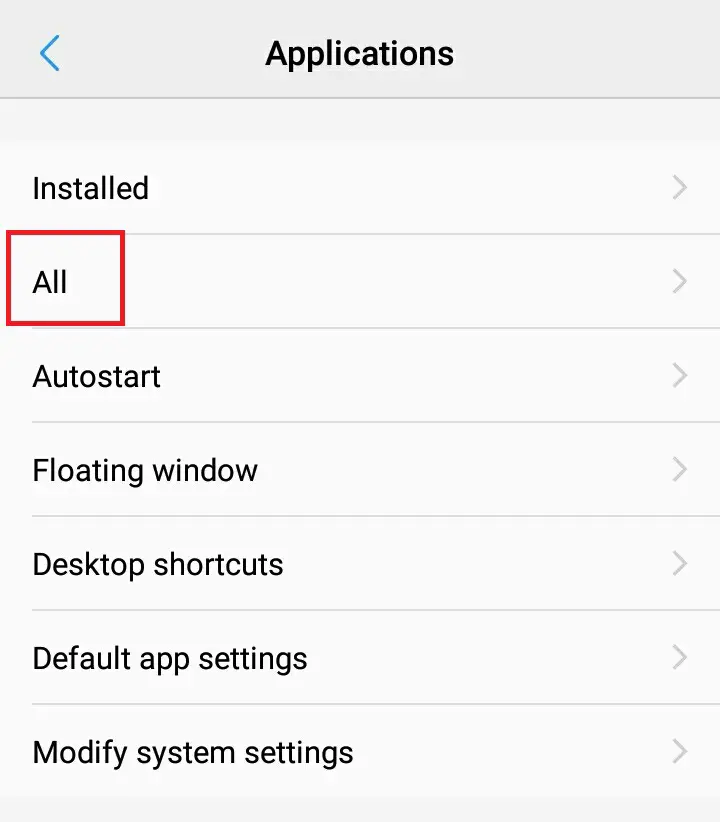
- Search in the list of given apps

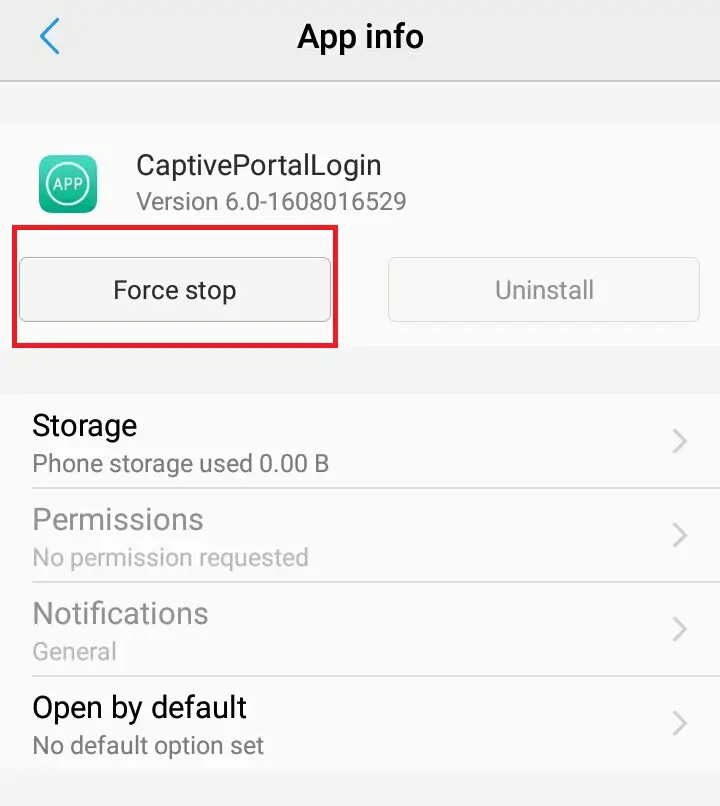
- Tap on that app and then tap on force stop
FAQs
- Does this app store our credentials or username or passwords when we log in to any website?
It only helps to establish a safe connection with the open networks. It has nothing to do with your credentials. If you click on remember option that pops up during login, the website saves your data.
- Can it perform tasks other than making a secure connection?
Yes, absolutely. It can perform tasks like controlling signal bandwidth, putting some restrictions to download, block some users if programmed to do so.
- Can we make our captive portal?
Yes, we can design and build our captive portal. Under the company domain, individual purpose any field related if you want.
Conclusion:
Here we come to the end of this topic. I have given you have got enough details about the captiveportallogin. User encryption and data breach are increasing day by day. To stop this, these kinds of applications are making ways for safe internet surfing. Creativity with integrity makes a perfect knowledge sketch. This article goes from history to a new era, from server requests to the web workflow.
This app comes from the cybersecurity domain. The field is gaining more and more popularity with an increasing number of developments and individuals connecting to it. It has huge community support to help new enthusiasts. I have a request to draft you. Please make sure about the sites you visit are safe. We are ignoring this issue. Our credentials are most important and most valuable. Black Hat Hackers make deals for millions of dollars selling personal data on the dark web or deep web.


